Sorry, something went wrong. Can you please try again? Or please send us a note at sales@fylehq.com, and we’ll get you started.
Sage Expense Management is committed to securing and encrypting all account, expenses, card, and employee information. What's more, you have complete ownership of your data at all times.
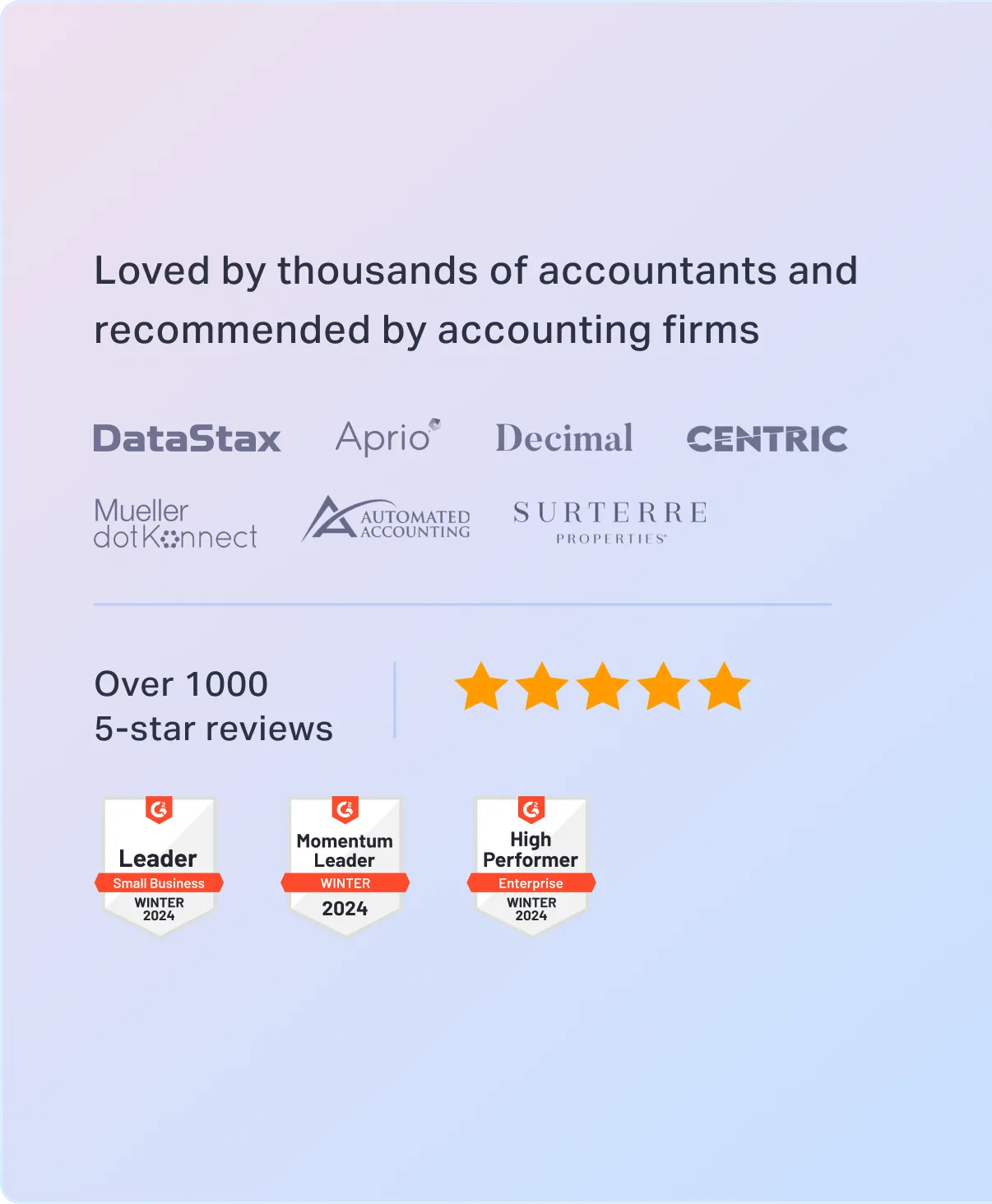
 1775+ reviews
1775+ reviews










User authorization
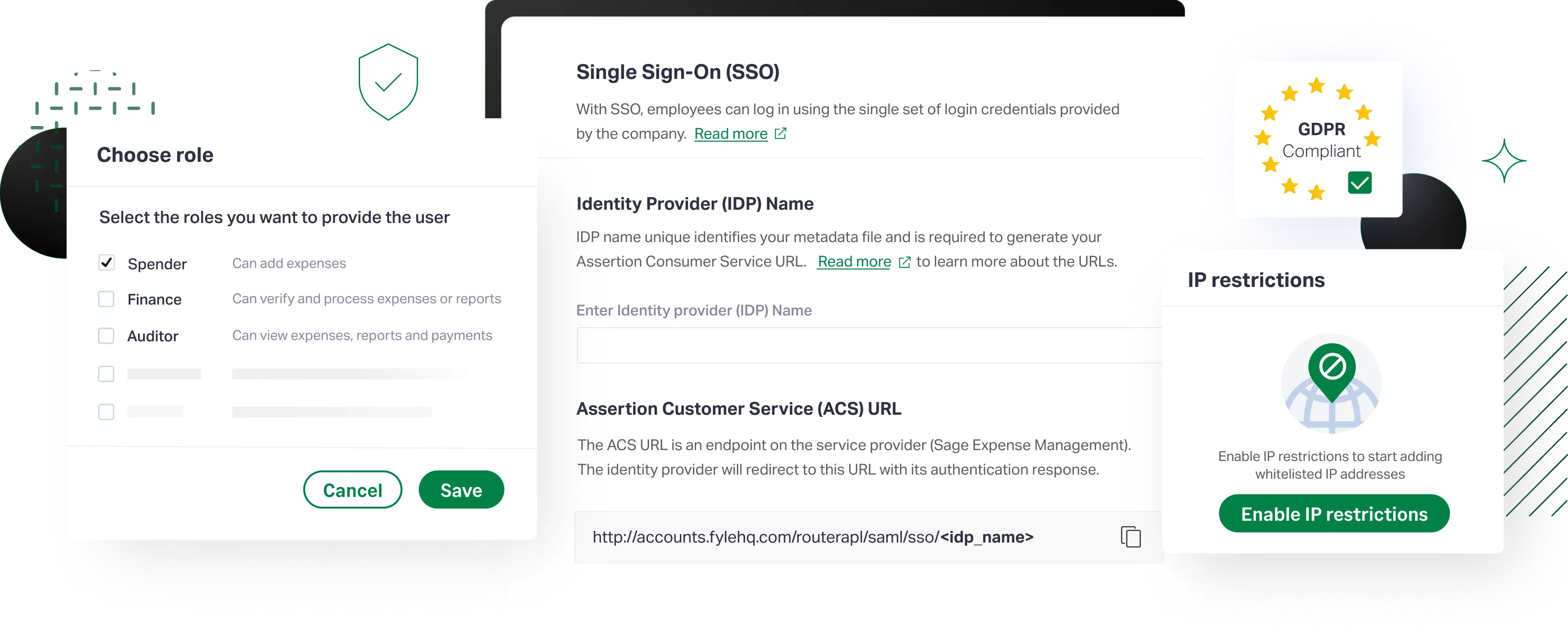
We facilitate the exchange of user authentication and authorization data across secure domains using Single Sign-On (SSO). Sage Expense Management uses SAML 2.0–based SSO to enable secure, centralized access for your organization.
Password encryption
All passwords are salted and hashed using SHA-256 cryptographic function. This is a one-way function and the original password is never stored at Sage Expense Management. We also encourage the use of strong passwords with a mix of alphabets, numbers and special characters.
GDPR compliance
Sage Expense Management has been GDPR compliant as of May 25th, 2018. We do not store any sensitive and personal information of our EU clients outside of EU allowed regions. All third-party services that Sage Expense Management uses are also GDPR compliant.
SOC 2 Certification
Sage Expense Management is now SOC 2 Type 1 and Type 2 certified. This means we have the infrastructure, controls, and processes to protect your data from unauthorized access from within and outside the firm. To learn more about the certification, click here.
IP access controls
Admin users are privy to almost all of your sensitive data, which can be taken advantage of. Sage Expense Management protects against any potential data breaches or threats by restricting access based on their IP address.
Role-based access
Each user is allocated a unique role as soon as they are added into Sage Expense Management. Each of these roles have visibility only to data that pertains to them. For example, a travel agent will only be able to view travel bookings that are assigned to them.
Data retention and control
We delete all our customers' data 30 days after the termination of the contract. Our clients own their data and are free to take backups or export data in standardized formats (CSV,PNG, PDF,JPG) at any point of time.
Vulnerability testing
We routinely get our services checked by third-party vendors for any potential risks or susceptibilities every 6 months. They use industry standard Grey Box/Black Box testing and the results are shared on request.
Auditor role
Our auditor role allows you to keep your data safe during your auditing process. It allows read-only access to view the payments that are pending, in process or completed. This role can be disabled soon after auditing is done.
PCI DSS compliance
Sage Expense Management's PCI DSS compliance is an indication that we have the necessary safety protocols to store and process customer payment card information, without any risk.
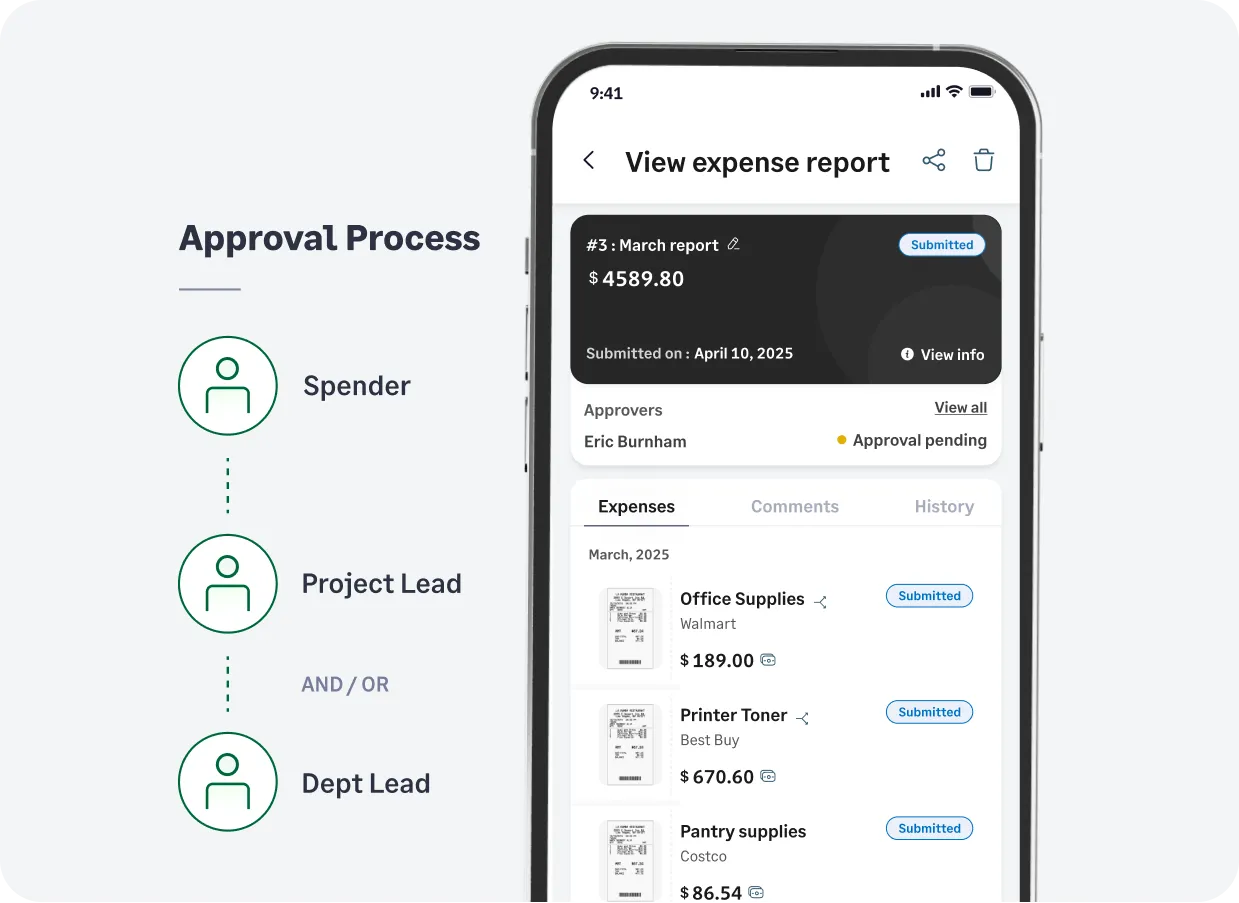
Configure automated approval workflows and enable managers to approve expenses right from their Emails, Slack or our Mobile App.
Learn more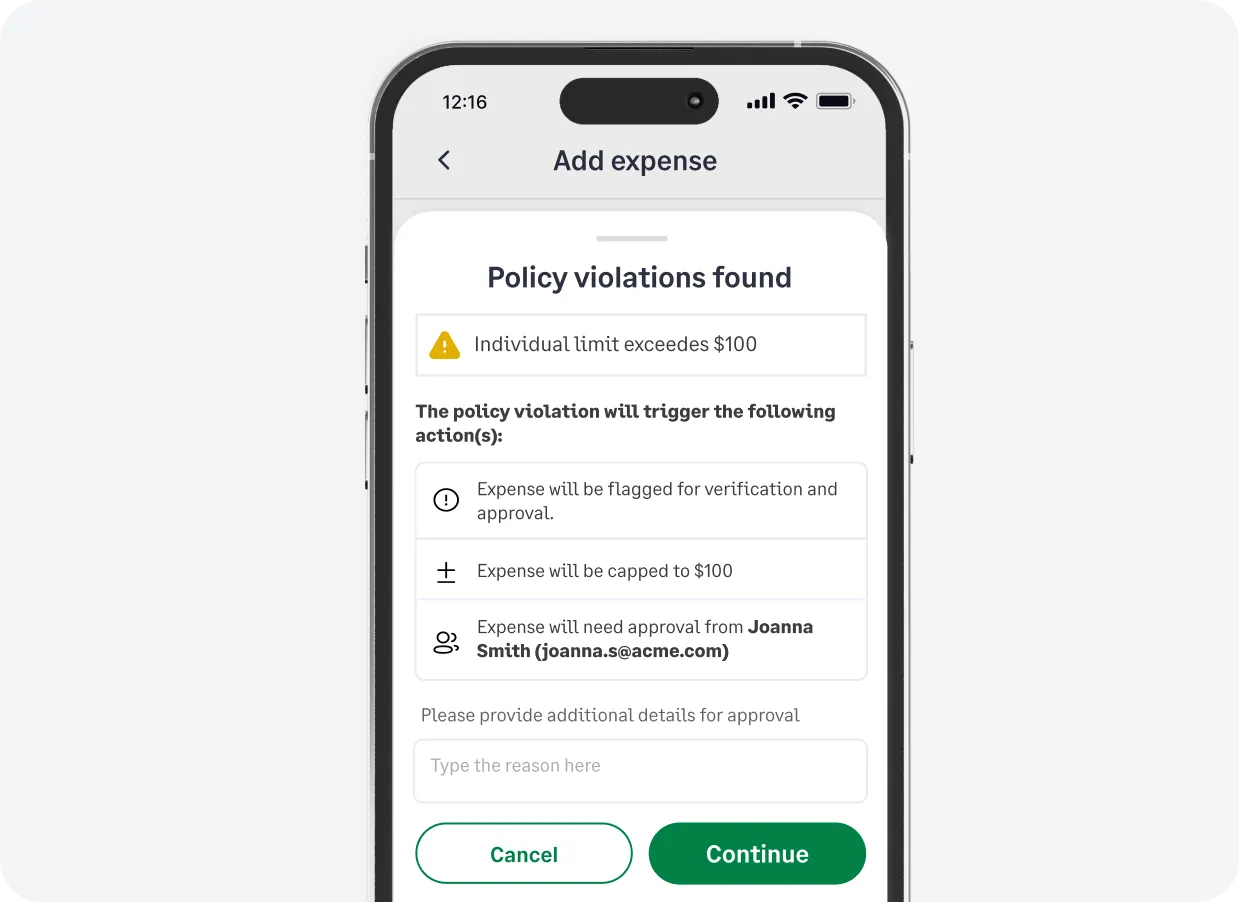
Our platform automatically checks if every expense complies with your business rules before it's submitted for approval. Detect duplicate or out-of-policy expenses instantly.
Learn more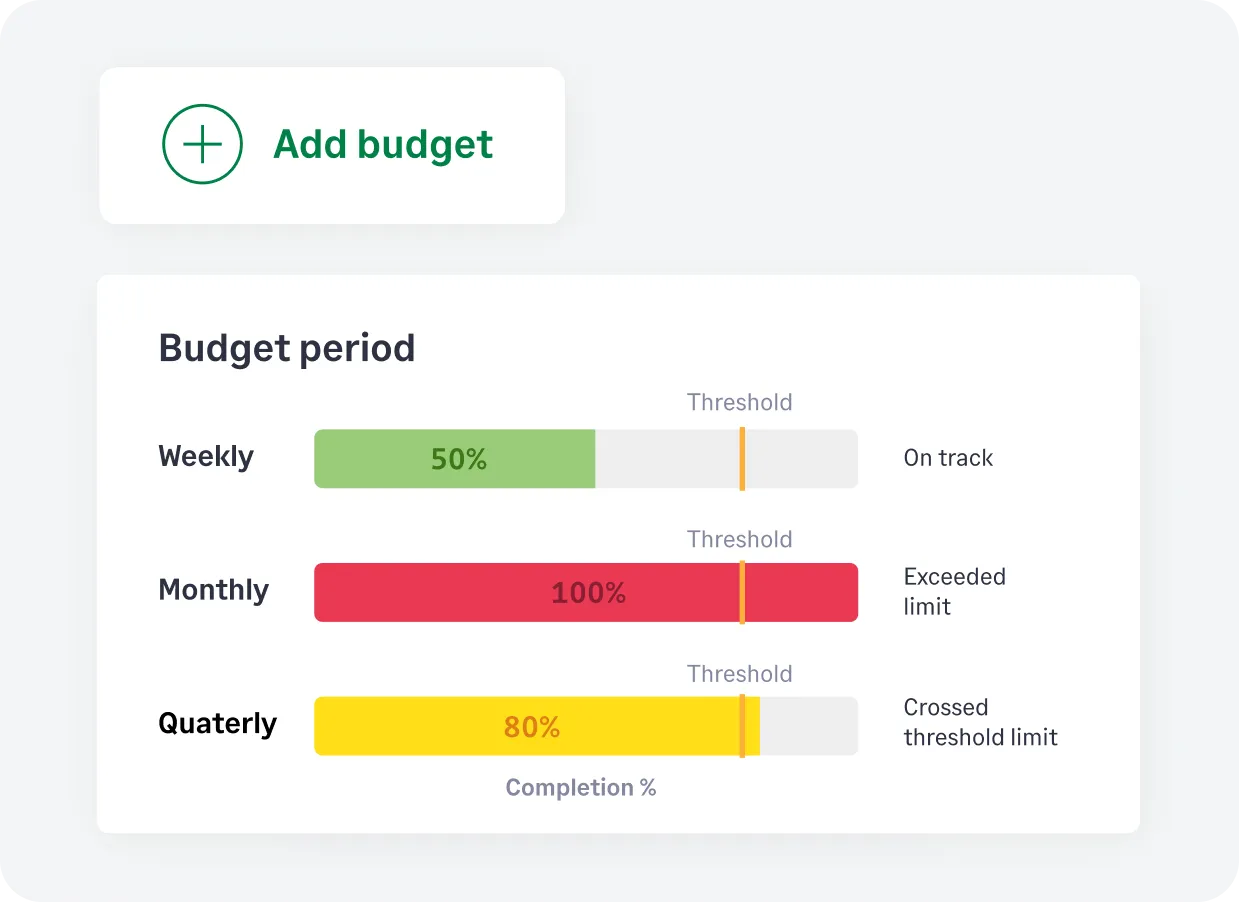
Set spending limits for categories, departments, projects, or cost centers. Choose weekly, monthly, quarterly, or annual limits. Get real-time email alerts when expenses near or exceed your thresholds.
Learn more